Oracle Reports: My First CVE
In 2018, I had some downtime between work projects, so I waded into the world of bug bounty programs. I learned that I’m not a great bounty hunter: I only found 3 payable bugs after investing a lot of bug hunting time. On the upside, I found a bug in Oracle Reports that eventually turned into… my first CVE credit!
Discovery
Synack quickly became my favorite program: very friendly to researchers in terms of scope, feedback, and payouts. On one of the engagements, I discovered a customer running Oracle Reports. Now, I don’t really know anything at all about Oracle reports and this particular customer seemed to have a very basic instance, but I quickly found a really obvious reflected XSS vulnerability.
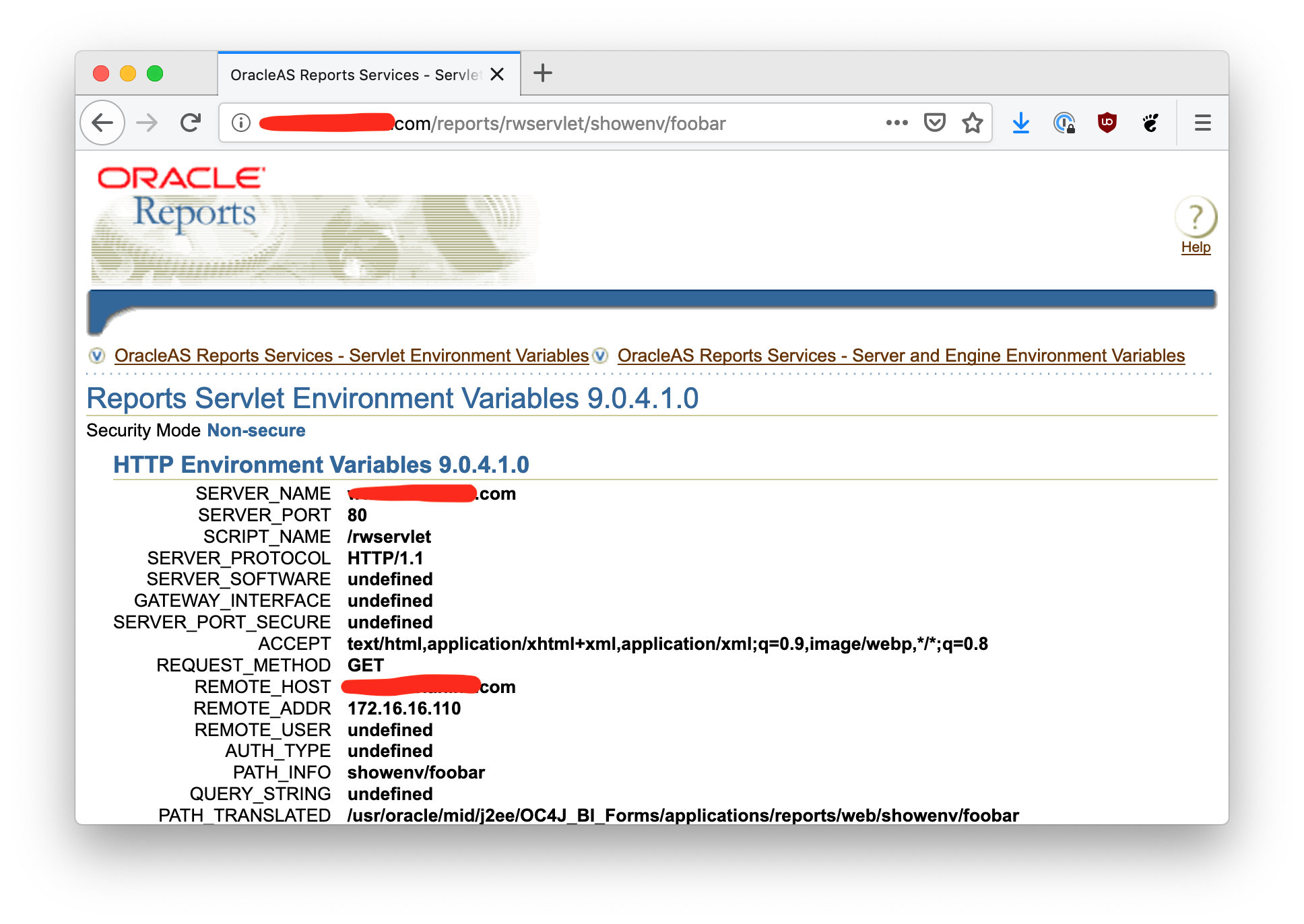
The XSS vulnerability exists on the /reports/rwservlet/showenv endpoint. Notice near
the bottom of the page there is a row that says PATH_INFO and displays showenv/foobar,
which appears to be taken out of the URL. But what if the URL contains a script tag?
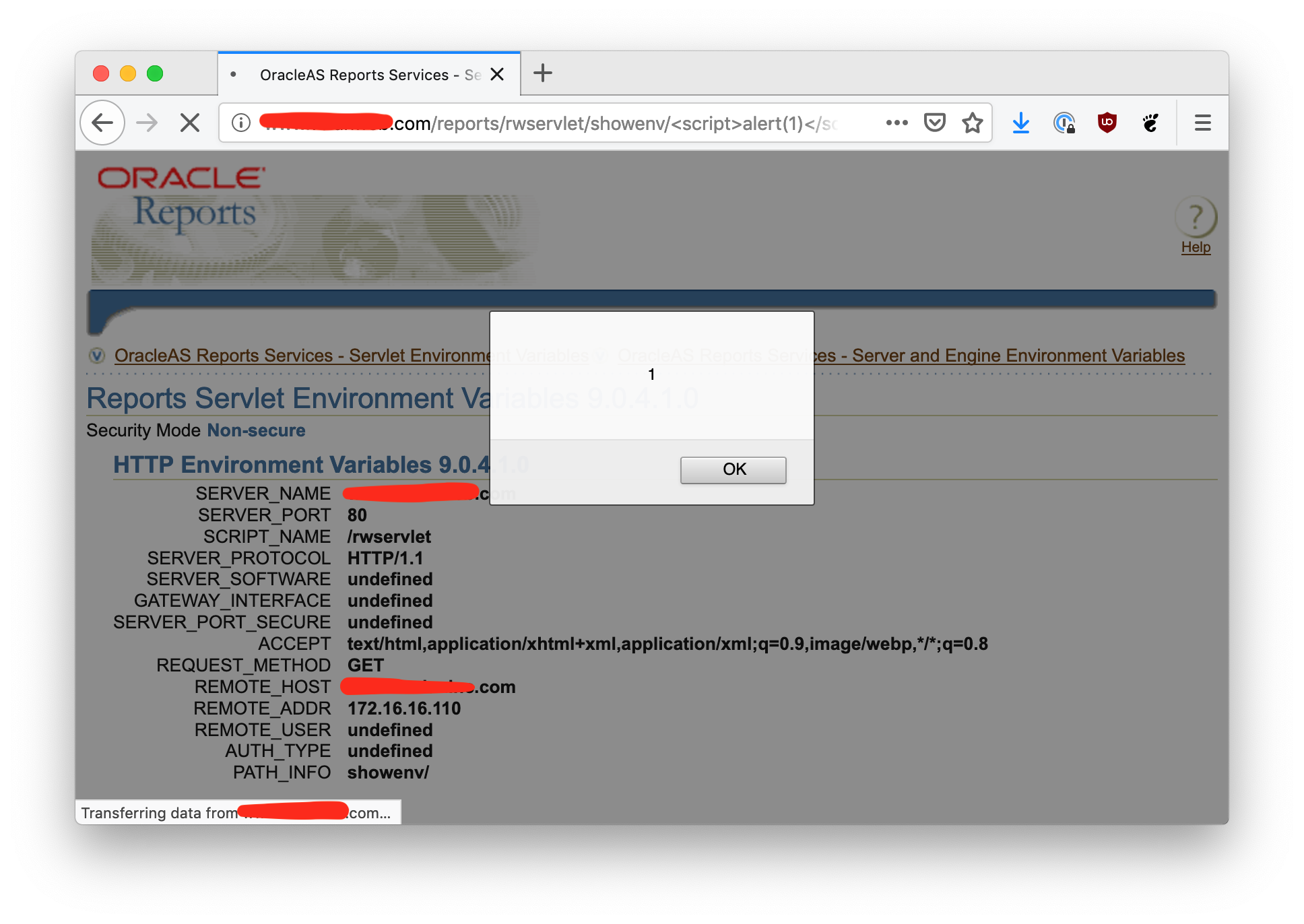
This is a really trivial XSS, but the bug bounty program I was in wouldn’t award a payout for reflected XSS unless a specific harm can be demonstrated, such as credential theft. If, for example, Oracle reports was running on the same origin as some other application that had weak cookies, then perhaps this attack could be used to steal session tokens. But in this case I was unable to determine anything else running in the same origin, so I didn’t submit a report to SynAck.
Disclosure
So what to do with it, then? I’ve never been in the position of discovering a vuln in a commercial product, so I thought, “hey, why don’t I try that unique form of infosec masochism where I responsibly disclose this to the vendor?” It’s a rite of passage, after all.
I typed up the details, PGP’ed everything, and sent it off to them on April 9, 2018. I’ve always worked at small companies, so maybe I’m out of touch with corporate America, but I naively assumed that a tiny bug like this would be easily and quickly fixed, right? Right, people?!
Nope. Oracle would send me an automatic update e-mail once every month. Every month, it would say the same thing:
Months rolled by. I briefly considered disclosing the bug before Oracle patched it, but then I just stopped caring. Finally, on Jan 11, 2019, I got another update from Oracle with the news I’ve been waiting for!
And to top it all of, they even assigned a CVE number: CVE-2019-2413. I’ve never had a CVE credited to me before, so this was a small nerd thrill for me. It turns out that another individual reported the bug at the same time as me, so we both got credit. My co-discoverer, Mr. Mohamed Fouad, also published a PoC on the Exploit Database.
It’s been so long since I reported this that I misplaced all my of original materials. It took me a few minutes to figure out how to decrypt the e-mail I sent to Oracle last year and I was bummed to find out that the screenshot I sent them was ridiculously small and wouldn’t be suitable for blogging at all.
Luckily for me, this bug is easy to find via Google Dorking, so I found another vulnerable instance online and made new screenshots (the ones you see above!). Some of the sites I found on Google look like they might really be vulnerable to credential theft as a result of this vulnerability. Hopefully those sites join a bug bounty!